Kubernetes vulnerability prioritization
Surface your top priorities from cloud native security noise
Are you able to understand the top priorities across the container, cloud, RBAC, network, public cloud, Kubernetes and runtime components of your Kubernetes environments? Do you have real-time context ?
With RAD Security threat vectors, your top risk is made obvious through a real-time, connected view of Kubernetes.
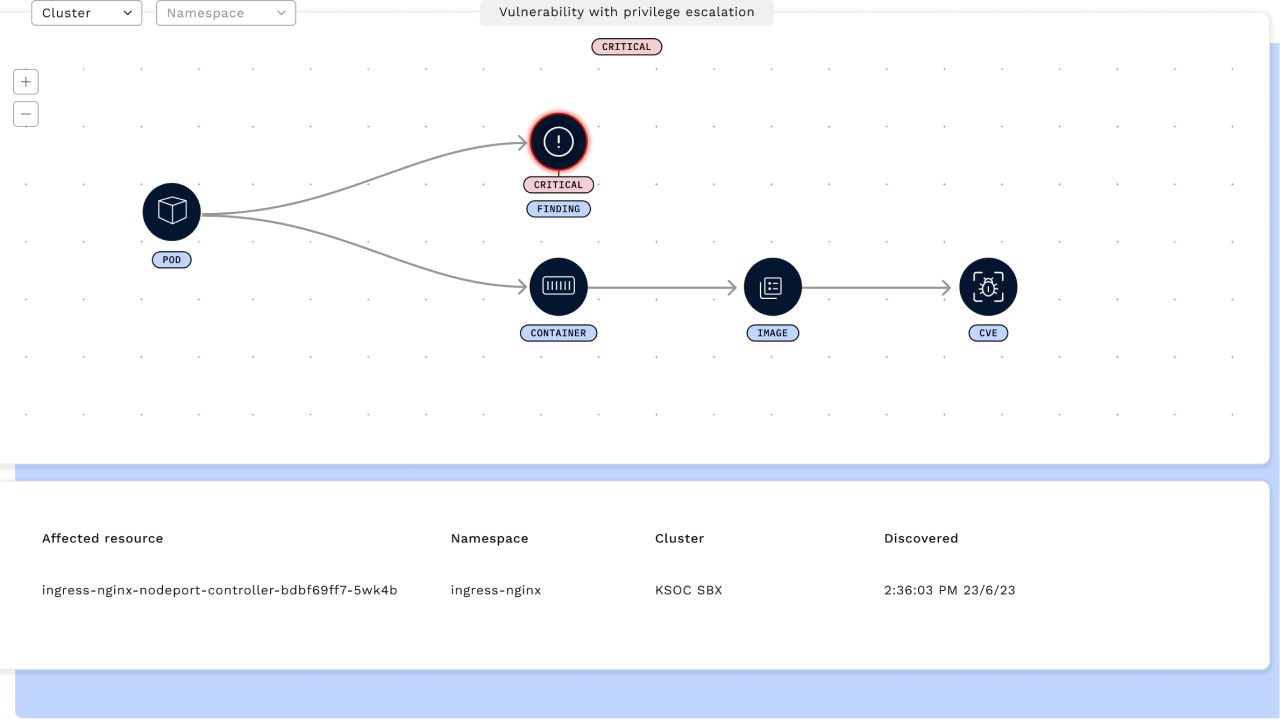
Manage and prioritize vulnerabilities in your Kubernetes environments
Free your security talent with automated vulnerability prioritization
The most experienced security experts are often tasked with the manual work of synthesizing large amounts of data across environments. Automate this work for your Kubernetes environments and save days of work for your top talent.
Empower engineering teams with remediation strategies
The engineering team building in Kubernetes every day is the resident Kubernetes expert. RAD Security provides remediation guidance that ‘speaks Kubernetes’ so you can get engineering actively engaged in the remediation process.
Enable all expertise levels to manage Kubernetes threats
The staff shortage in security means that every security team has a wide range of expertise, especially when it comes to cloud native security. RAD Security creates an easy view of your highest priority vulnerabilities in Kubernetes, with optional deep dives so those of any skill level can make an impact.
Consolidate cloud native security vendors for simplified vulnerability management
While vendors focus on silo’d pieces of cloud native security, attackers work fluidly across your environment. With a connected view across Kubernetes components, RAD Security threat vectors are the most efficient way to improve your cloud native security posture, allowing you to consolidate vendors.
RAD Security threat vectors show your top priority risk by connecting the relationships across RBAC, image CVES, runtime, public cloud, Kubernetes misconfigurations and the network
Kubernetes vulnerability prioritization
Threat vectors populate in minutes
Save days of manual work connecting risk across Kubernetes components
CVE Exploitability
Prioritize CVEs based on their exploitability in running containers
Get Kubernetes-native remediation guidance
In a view that engineering will understand, down to the line of code in the manifest

