A RADical New Approach:
Behavioral Cloud Native
Detection and Response
RAD Security creates behavioral fingerprints of your unique good behavior across the software supply chain, cloud native infra, workloads and identities, to detect zero day attacks and sharpen inputs into shift-left and posture management.

The RAD Security Platform


What is your cloud native detection and response challenge?
Can you verify workload behavior in your CI/CD pipeline?
Can you prioritize CVEs based on their usage in runtime?
Can you verify the results of shift left initiatives in real-time?
Can you detect drift from your workloads' unique, good behavior?
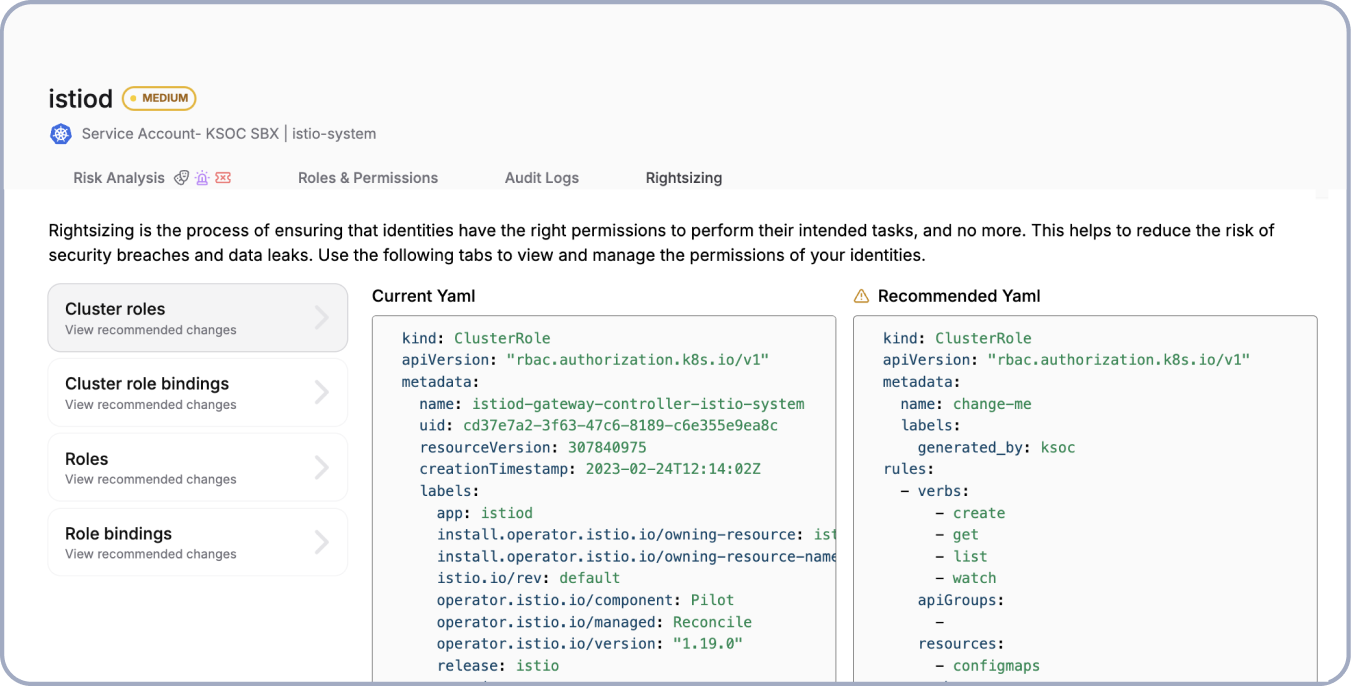
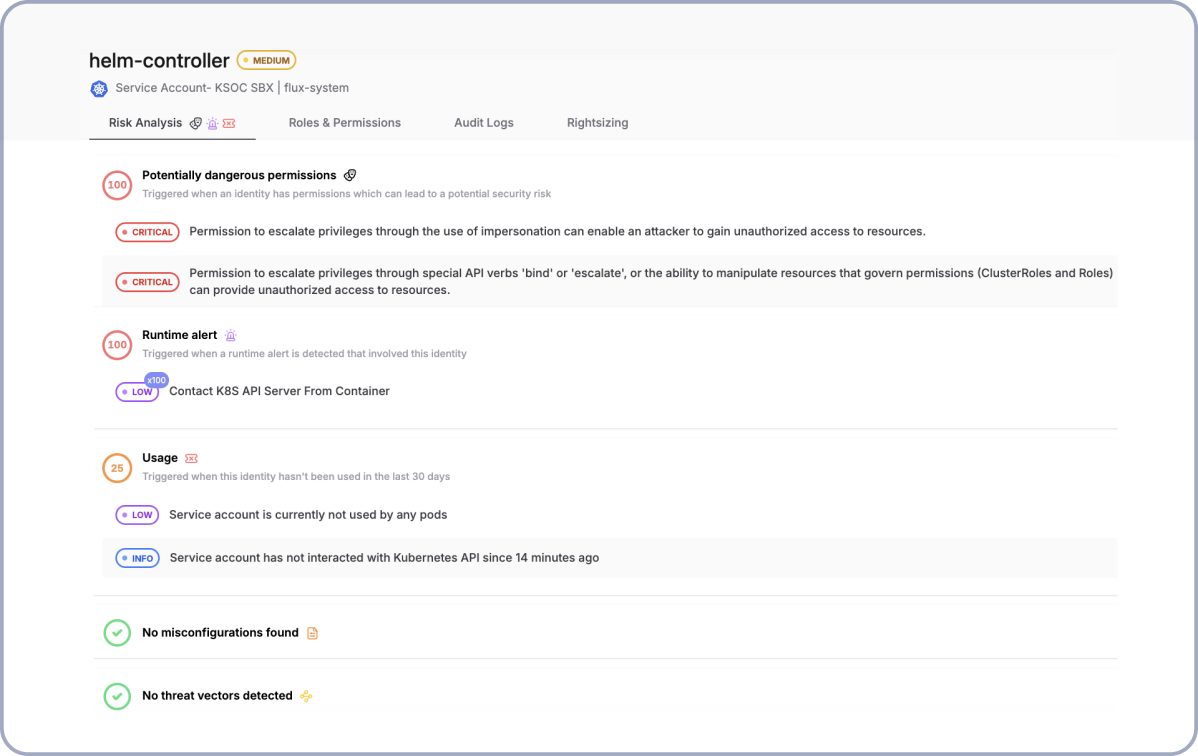
Can you automate user access reviews for Kubernetes RBAC?
Can you use a low privilege eBPF agent that won't break your app?
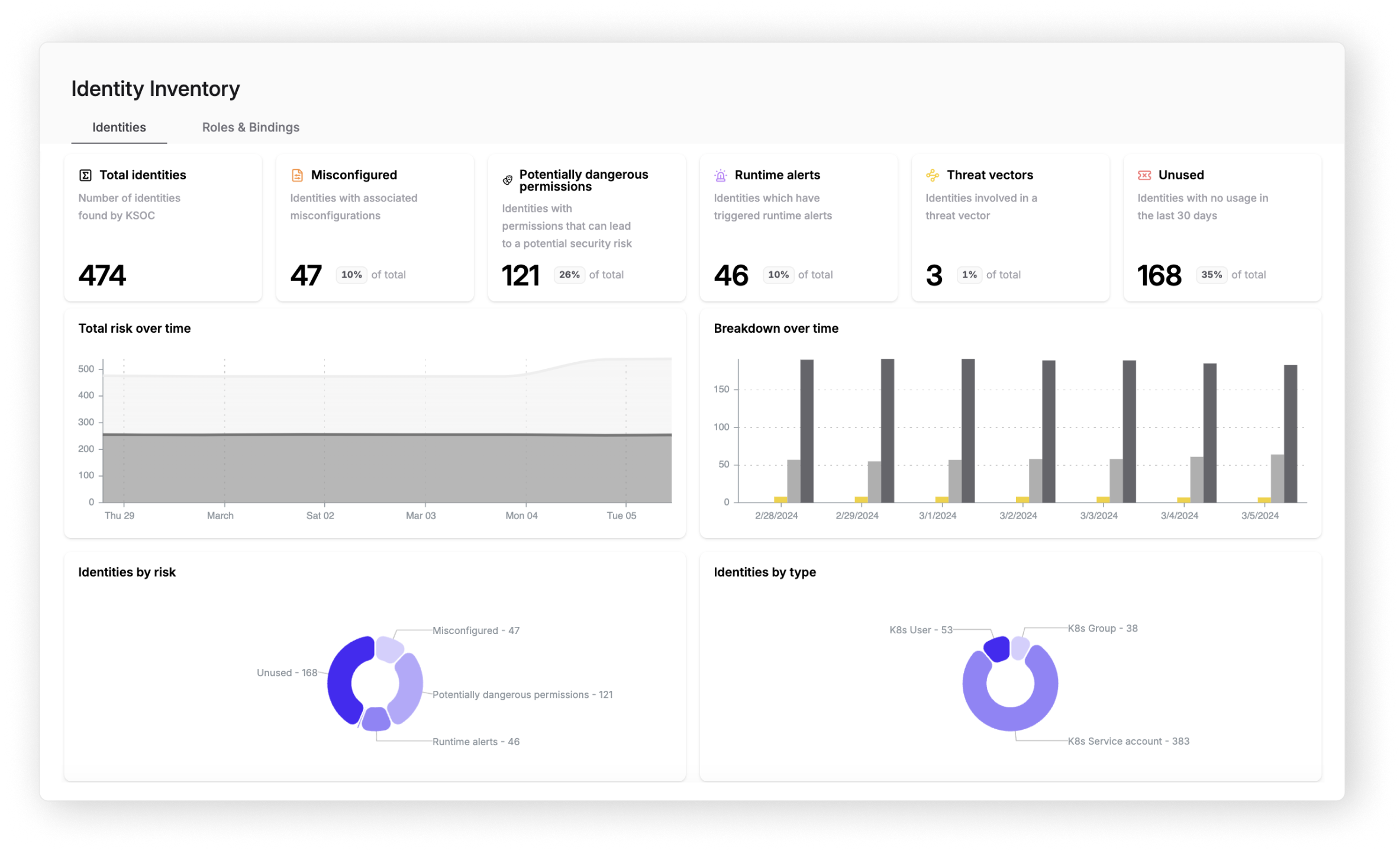
Prioritize Your Riskiest Identities
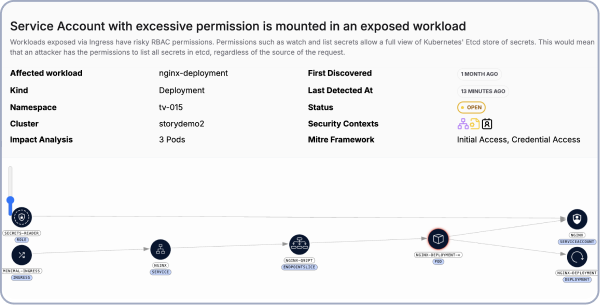
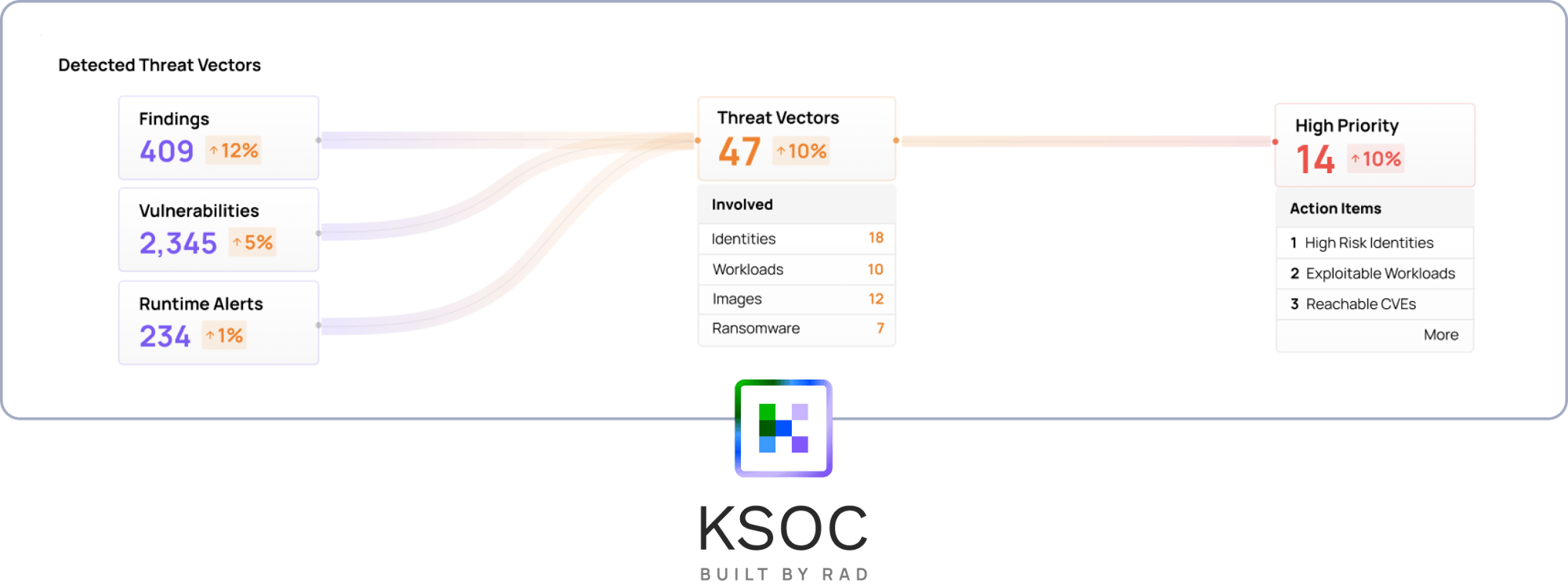
Threat Vectors
- Prioritize your top risk in real-time across runtime, the network, image CVEs, K8s misconfigurations, the cloud and identity
- 5 Minute installation and configuration
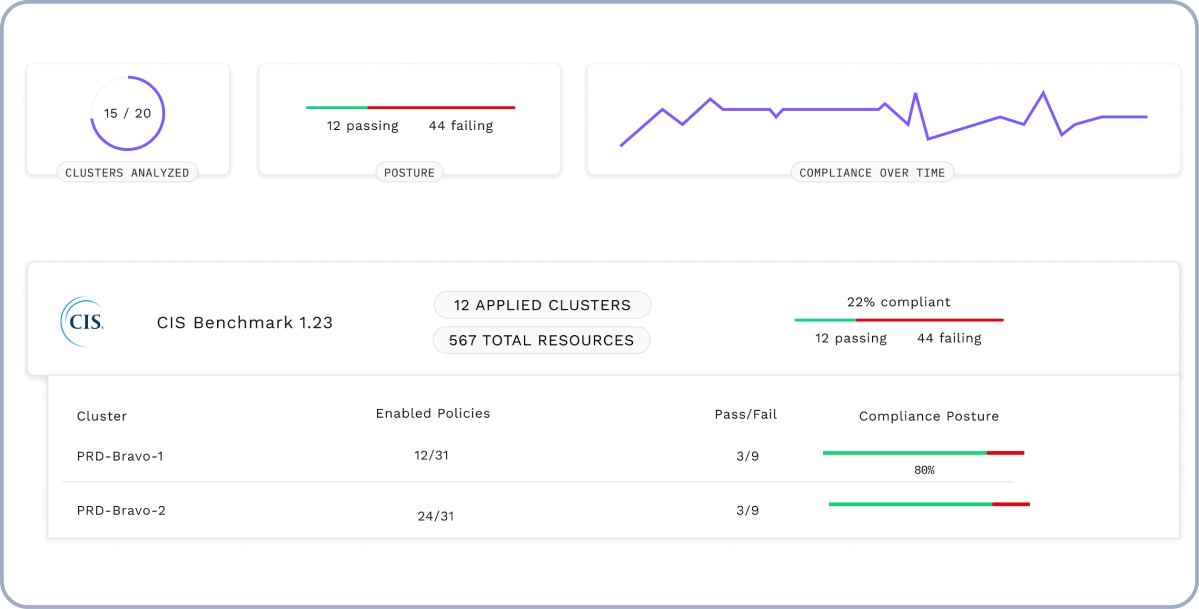
- Real-time, to-the-second, view of Kubernetes misconfigurations, tied to the Kubernetes lifecycle
- Identify vulnerabilities in running images
- Risk Explorer visualizes and filters a live-stream view of the environment

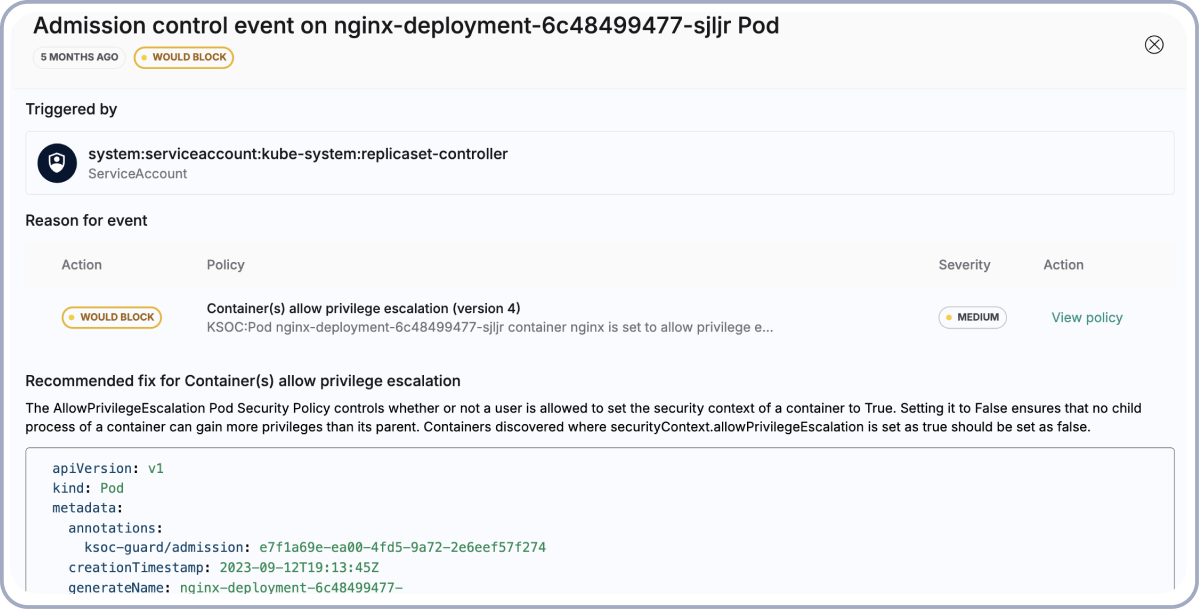
Guardrails and Admission Control
- Prioritize CVEs based on exploitability in runtime
- Admission control that is OPA compatible
- In-cluster policy enforcement and optional 'dry run' mode
- GitHub Actions CI Worklflow to remediate policy or scan for CVEs earlier in the lifec
- Identify vulnerabilities in running images
- Manage workload policy centrally in the CI
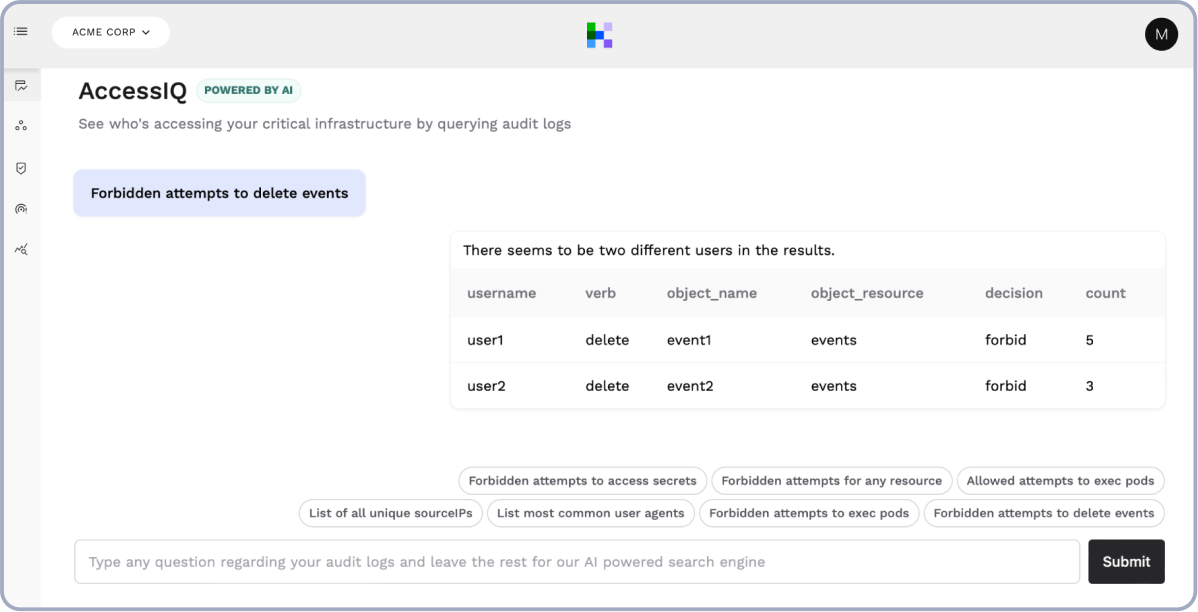
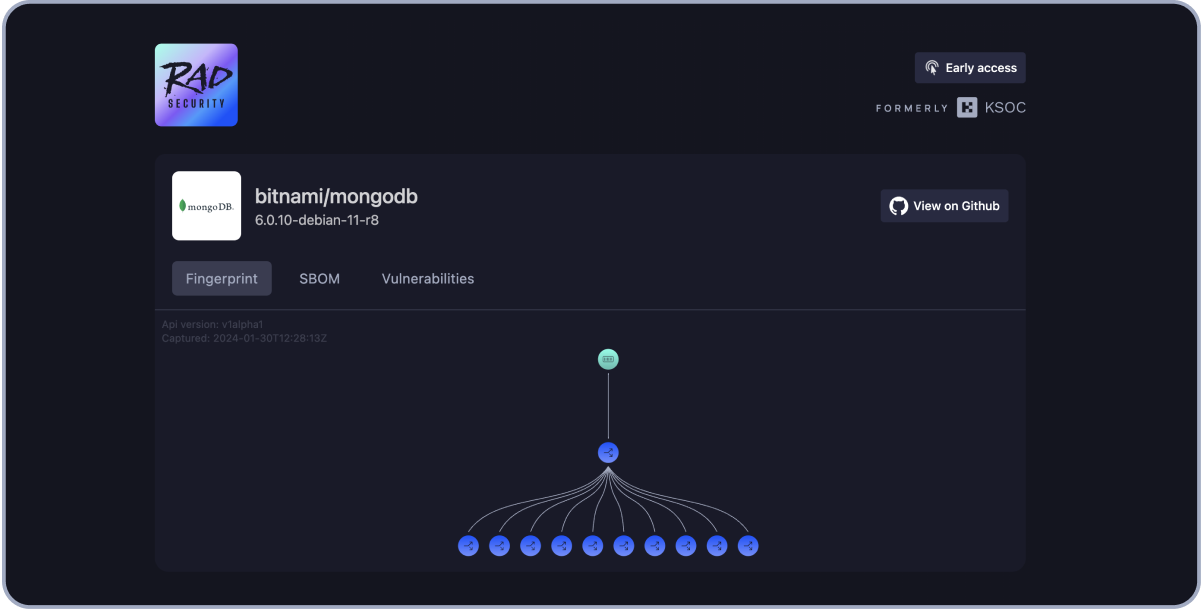
Software Supply Chain Attacks
- Free online fingerprint catalog for popular open source images
- Fingerprints show containers, processes, child processes, programs and files that are executed at runtime
- Create and sign your own workload fingerprints for vendors using your software
- Use workload fingerprinting to verify your CI/CD pipeline and protect against attacks like SolarWinds

Eliminate Zero Days in Runtime
- Generate your own unique cloud native workload fingerprints
- Detect material change from behavioral fingerprints to identify active incidents
- Low privilege eBPF agent with minimal overhead
- Historical context across the network, cloud, Kubernetes, and runtime for quick investigations
- Respond with alert, quarantine, or other actions on the workload
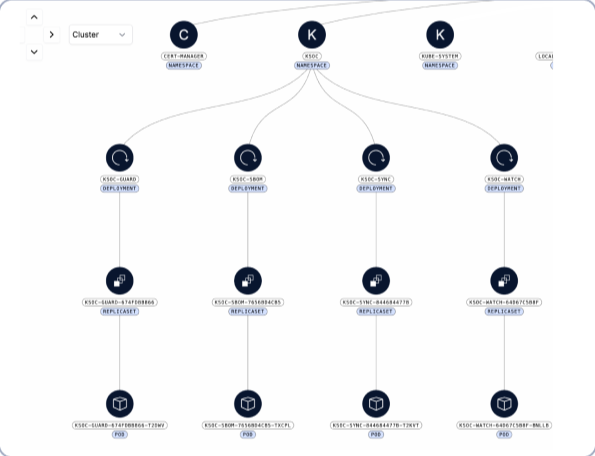
Cloud and Kubernetes-Native Operations
Seamlessly integrate into the engineering workflow
- Real-time, in-cluster components include Kubernetes manifest, RBAC, network, container images
- Install via an effortless cluster plugin
- Multi-tier account management
- Low memory and CPU footprint
- Uses a combination of in-cluster, runtime and external agent-less components
Integrations
RAD Security supports all managed Kubernetes platforms and DIY Kubernetes clusters. Easily connect RAD to your team’s development, management or security response tools via our public REST API.