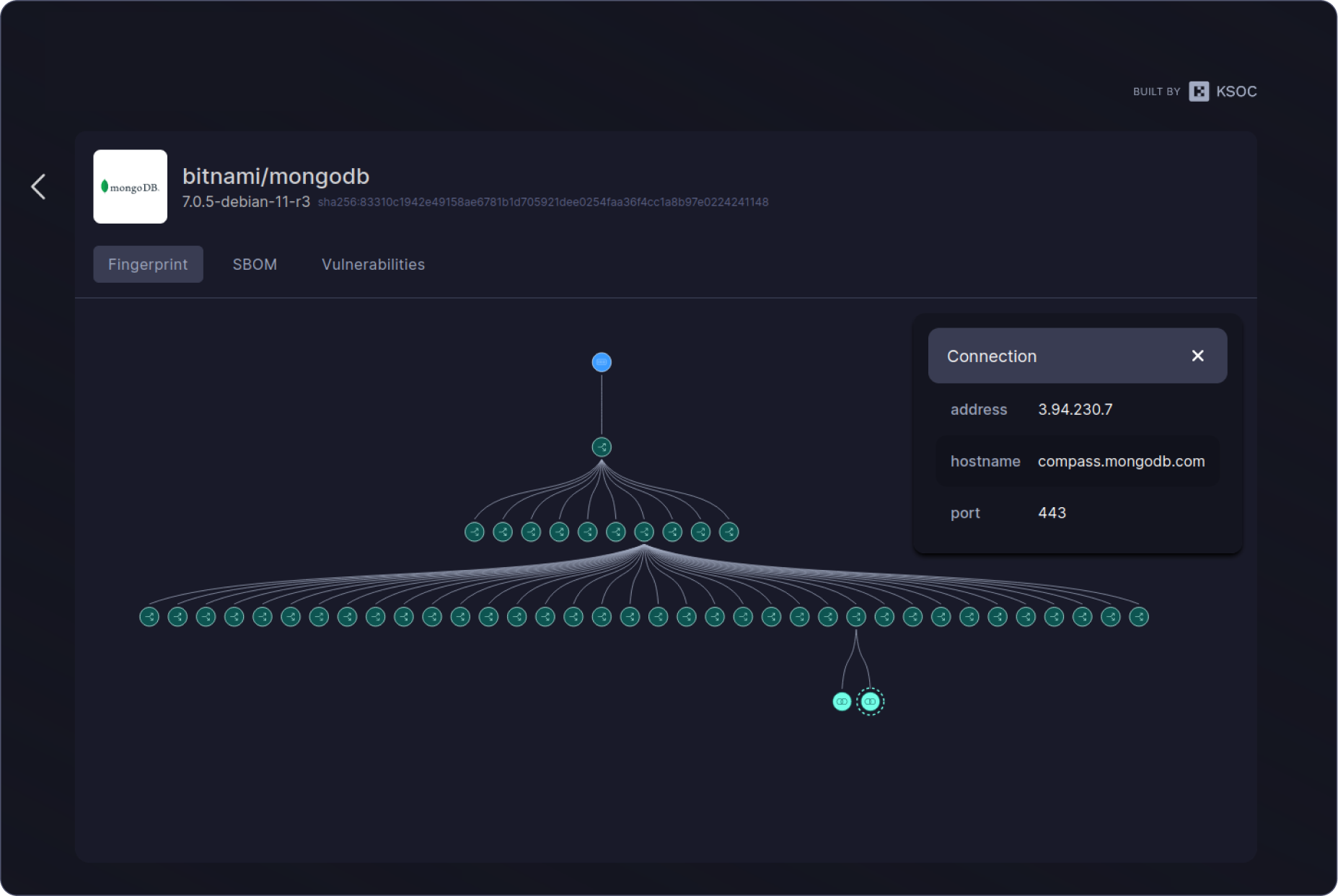
What are cloud workload fingerprints?
Cloud workload fingerprints are the output of the RAD security standard, which uses eBPF to codify the baseline runtime behavior of the processes, programs and files in a cloud workload. This baseline workload fingerprint is portable and can be used as far left as the software supply chain in CI/CD, giving DevSecOps teams and security engineers a transparent, verifiable defense against the next wave of zero day software supply chain and cloud attacks.
Use-cases
Software Supply
Chain Security
Behaviors captured and analyzed by eBPF form a unique, verifiable fingerprint that can be used throughout the SDLC to ensure integrity
Zero
Day Detection
Use a verifiable fingerprint of cloud workload behavior for a ground zero representation of what should be running in your environment
Runtime
Protection
Verified runtime security fingerprints via a light-weight eBPF agent make automated, contextual response actions possible and lower false positives by 99%