Intro
Today three new Kubernetes CVEs were released pertaining to the ingress controller for nginx. They are each individually rated as high in severity, and involve manual configuration fixes that could be relevant across a large environment. KSOC can help you automate the identification of vulnerable ingress objects while enforcing secure configuration with an admission control policy.
What is the nginx ingress controller?
The Kubernetes Ingress API has been a stable feature in Kubernetes since v1.19 was released in 2020. The Ingress API was originally developed to simplify the process of routing http(s) traffic from outside a cluster to any of the various services inside a cluster. Today, the Ingress API requires an accompanying ingress controller, whose job it is to define the map of a path to a pod in a Kubernetes cluster. This map is drawn with an ingress resource, or an ingress object. The below screenshot shows a minimal spec for defining an ingress resource:
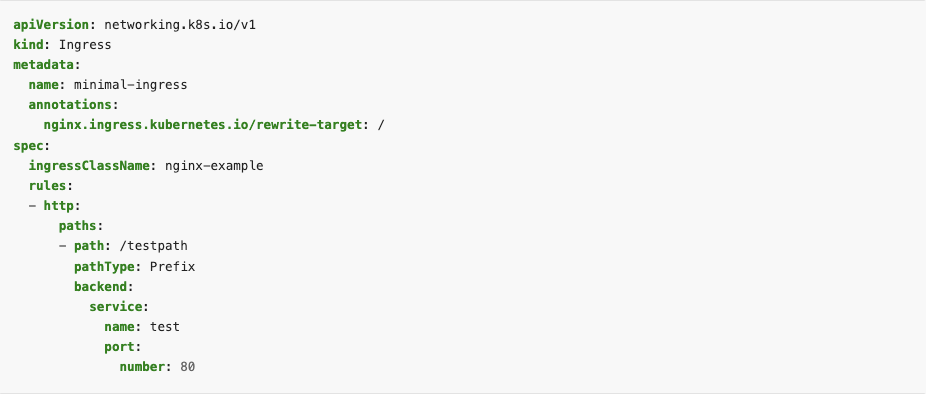
Ingress controllers can be specific to a particular cloud provider or more generally applicable. For example, a Kubernetes environment running on AKS requires the AKS Application Gateway Ingress Controller. The nginx ingress controller is a popular, universal tool that is not specific to a cloud provider, and also can help with API Gateways and load balancers at the cluster’s edge.
How do the vulnerabilities work?
CVE-2022-4886, CVE-2023-5044 and CVE-2023-5043 are all applicable to the nginx ingress controller.
Anybody who can create or update an ingress resource could obtain the credentials of the controller because of a sanitization bypass bug. If the controller is still configured in default mode, this means that person could have access to all the secrets in the cluster.
Anybody using nginx.ingress.kubernetes.io/permanent-redirect to modify the status code used for permanent redirects in an ingress object, could inject arbitrary code to obtain the controller’s credentials.
Anybody using the nginx.ingress.kubernetes.io/server-snippet annotation to add custom configurations to the Server configuration block in an ingress object could inject arbitrary commands and obtain the controller’s credentials.
Are you affected, and how to mitigate?
If you are not using an nginx ingress controller, you are not affected. If you are using nginx-ingress, unfortunately, the recommended mitigation options require reconfiguration that, in many cases, might be manual, and might be required across multiple ingress objects and ingress-nginx annotation fields.
For CVE-2022-4886, the recommended mitigation is to ensure that, by default, the pathType associated to the path in the ingress resource (or object) is chosen is Exact or Prefix (neither of these options leave room for typos or errors, unlike the ImplementationSpecific option which could allow for paths from other resources). This would prevent the specific sanitization bypass mechanism, by preventing custom directives from being an option to bypass the sanitization in the path. In this case, admission control is also a possible mitigation option.
For CVE-2023-5044 and CVE-2023-5043, the recommended mitigation is to set the --enable-annotation-validation flag, which would restrict what is allowed inside the ingress-nginx annotation fields. Unfortunately, in this case, admission control is not yet a mitigation option, as the admission controller will not be able to validate the annotations.
How KSOC can help
Given the broad usage of ingress resources, it is important to automate the identification and any fixes, as possible for these three highly rated vulnerabilities. KSOC can identify exploitable nginx ingress configs, and provides an option to enforce secure configuration with an admission control policy that blocks an exploitable ingress resource, in the case of CVE-2022-4886.
Below is an example detection of this issue, as well as the suggested remediation advice in the manifest.
.png?width=1313&height=112&name=image%20(12).png)
.png?width=1432&height=758&name=image%20(14).png)
.png?width=1440&height=348&name=image%20(13).png)
To identify your exposure today, request a free trial!
Conclusion
If you are using the nginx ingress controller, these new CVEs will require prompt, and possibly manual mitigation, without a way to automate the enforcement of a secure configuration. Reach out to us today to automate the broad identification of your exposure and put safeguards in place while you work to implement the mitigations.



