From the desk of KSOC's security research team:
The Kubernetes development team received reports that the Kubernetes API may have a Server Side Request Forgery vulnerability when using aggregated API servers. The team promptly patched multiple versions of Kubernetes in order to help remediate the issue, leaving it to Kubernetes administrators to upgrade their version of Kubernetes.
Impact:
CVE-2022-3172 is a medium rated vulnerability scoring a 5.1 on the CVSS scale. Affected versions of Kubernetes API Server will allow aggregated API servers to redirect client traffic to any URL. An attacker may attempt to use this to manipulate the client into performing unexpected actions or forwarding the client’s API server credentials to third parties. If an attacker is able to steal the Kubernetes API server credentials, they’ll be able to use those credentials to access internal cluster resources. This issue is significantly amplified if the attacker has cluster admin privileges. In a recent public internet scan (May 2022), Shadowserver ran a version scan of 454,729 Kubernetes API instances available to them on the public internet and 381,645 of those IPs responded with a 200 OK HTTP response code and disclosed version information in the response. Based on the scan performed, 341,731 (89.5%) of those API’s are running on Kubernetes v1.21 or older, which do not have a patch released. See their report here.
Detecting Exploitation attempts:
Kubernetes Audit logs are incredibly valuable for threat hunting within a Kubernetes environment. Audit log events can log the HTTP status codes via the responseStatus.code field. Searching for status codes 300, 301, 302, 303, 307, and 308 within your audit logs may indicate an exploitation attempt of this CVE.
Some environments may require redirect functionality from aggregated API servers however. If this is the case, security professionals should validate source and destination IP addresses of the redirection in order to look for anomalous behavior.
How can I tell if I am affected?
An initial fix was developed and released which blocks 3XX responses from aggregated API servers by default. This fix was released on September 9th. A secondary fix is targeted for release on September 21st, which will allow the server to send back 304 HTTP response codes as 304 Not Modified is not a redirect response code and is not applicable to this vulnerability. The resulting impact of blocking the 304 response code was documented in an upgrade from 1.25.0 to 1.25.1 where the standard metrics-server deployment will continually flood the kube-apiserver logs on a recurring basis. Details can be found here.
The following versions are known to be affected:
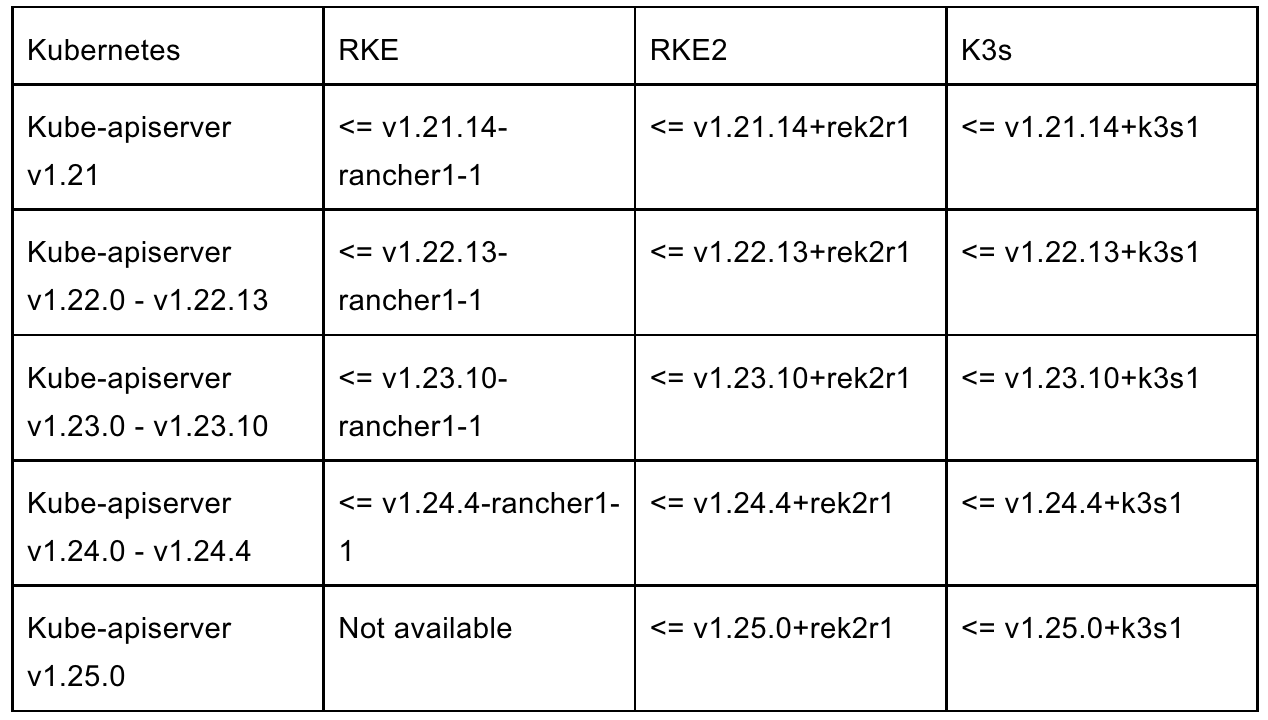
The following versions have applied the fix:
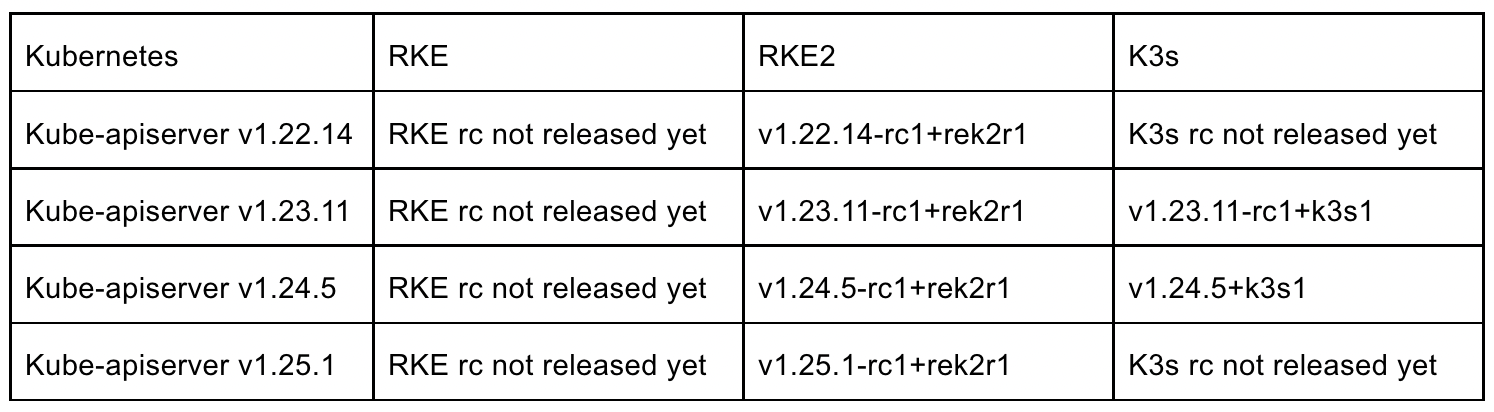
Rancher is maintaining an up to date list of patched versions here.
Potential impact of the remediation:
If your environment requires aggregated API servers to have the ability to redirect, set the –aggregator-reject-forwarding-redirect Kubernetes API server flag to false in order to restore previous behavior.
How can KSOC help?
KSOC can help detect and find vulnerable versions of the Kube-APIServer deployed across your clusters. Our robust policies include checks which would help minimize the exposure of vulnerabilities such as CVE-2022-3172 and can help you find and remediate issues in your environment through an in-cluster presence as well as container image scanning.
Help protect your Kubernetes environments today by scheduling a demo of the KSOC platform at https://ksoc.com/get-demo.



