TL;DR Summary
- CVE-2024-3094, otherwise known as the XZ Backdoor software supply chain attack, is considered the most sophisticated social engineering attack on open-source projects to date.
- An attacker or attackers, masquerading as maintainers of the popular open-source project XZ Utils, packaged malicious code in a software update. The goal of the attack was to take over remote code execution.
- This was a long-term, planned attack that took advantage of multiple components, including XZ Utils, sshd, and glibc.
- There have not yet been any reports of the exploit being utilized in the wild. You should definitely not update to the 5.6.0 and 5.6.1 latest versions - and if you did, downgrade to an un-compromised version.
- The attack underscores the need to capture a profile of your environment before zero days occur, versus relying on reactive, signature-based detection or anomaly detection that cannot detect normal processes and programs that are used for malicious purposes.
*Update - the Open Source Security (OpenSSF) and OpenJS Foundations issued an alert for social engineering takeovers of open source projects
What is CVE-2024-3094 (XZ Backdoor)?
The discovery of a sophisticated backdoor in XZ Utils, specifically targeting the liblzma component, has raised considerable alarms across the cybersecurity landscape.
At the heart of this malicious endeavor is a deceptively inserted script within the distribution tarballs, not present in the genuine upstream source.
This script executes under certain conditions during the build process, subtly altering the Makefile to execute obfuscated malicious code.
The intricacy of this attack becomes evident through the injection of obfuscated scripts in test files, which, when decoded, reveal the attacker's intent to manipulate the building process for nefarious purposes.
This backdoor was ingeniously designed to trigger only under specific circumstances, targeting x86-64 Linux systems built with GCC and the GNU linker, and notably within Debian or RPM package builds.
Its activation could significantly impact the performance of SSH logins, exploiting patched versions of OpenSSH to introduce delays, hinting at its operation.
This meticulously crafted supply chain attack serves as a stark reminder of the persistent threats lurking in open-source software distributions.
Who Was Behind CVE-2024-3094?
The attack involving the XZ backdoor was carried out by an individual or individuals operating under the name Jia Tan.
The attacker(s) gained the trust of the open-source community by contributing to the project over two years, eventually obtaining manager permissions.
This allowed them to insert the backdoor into the liblzma library, which is used by xz utilities. The true identity of Tan is still unknown.
How Was CVE-2024-3094 Discovered?
The xz backdoor was first identified by Andres Freund, who uncovered significant vulnerabilities in the liblzma library, a core component of the xz utilities.
Freund focused on tracing the specific modifications within this library that enabled unauthorized access. The technical analysis revealed that the flaw could be exploited to bypass security measures, allowing attackers to run arbitrary code on the affected systems.
What Were the Components of the XZ Backdoor Attack?
This was a long-term, planned attack that took advantage of multiple components, including XZ Utils, liblzma, sshd, and glibc.
What is XZ Utils?
XZ Utils is a widely used tool on Linux systems to compress data like release tarballs (a compressed archive file), software packages, which is helpful in the process of backing up data and archiving files. It is based on the LZMA2 compression algorithm.
What is liblzma?
liblzma is a library used for compressing and decompressing data in the LZMA (Lempel-Ziv-Markov chain algorithm) and XZ formats. The backdoor discovered in the XZ Utils exploited vulnerabilities in liblzma.
What is SSHD?
Remote code execution on a machine, or encrypted communications over an insecure network, is possible through sshd, or the Secure Shell Daemon application (SSH daemon or sshd). Alternatives include rlogin and rsh.
What is glibc?
glibc is a C library for Linux distributions, providing mostly low level functionality to the operating system. It provides an interface for system resources like files, networks and memory, so software can be more easily developed across different platforms.
Am I Vulnerable to CVE-2024-3094?
The XZ Backdoor attack relies on the following pre-requisites:
- Only activating on deb/rpm package builds
- You need to be running a distro that uses glibc (for IFUNC)
- If you're running a publicly accessible sshd, then you are - as a rule of thumb for those not wanting to read the rest here - likely vulnerable
Luckily, there have been no reports of the exploit being utilized in the wild.
You should not update to the 5.6.0 and 5.6.1 latest versions - and if you did, the guidance is to downgrade to an un-compromised version.
How to Check if You are Affected
First, the simplest check is to find your version of xz utils. You can also use an XZ Backdoor scanner and detector, which looks for whether the malicious version is running as well as whether or not the machine is vulnerable (aka has an sshd payload that could be impacted).
You can also check whether the Liblzma library has been opened by an SSH server using this command, which will tell whether the version of Liblzma loaded in memory (if any) is one of the affected versions :
lsof -p $(ps -aux | grep 'sshd' | grep 'listener' | awk '{print $2}') | grep '\.so' | grep 'liblzma'
Using RAD Security Behavioral Fingerprints to Detect and Respond to CVE-2024-3094
The XZ attack vector underscores the challenges in detecting and mitigating supply chain threats. However, a behavioral eBPF runtime security agent represents a beacon of hope in this scenario. By leveraging RAD Security’s deep observability capabilities across the Linux kernel, customers can detect anomalous behaviors indicative of a compromise.
For instance, unexpected modifications to the build process or the execution of obfuscated scripts would deviate from standard operation patterns, triggering alerts. Furthermore, RAD Security’s ability to monitor system calls in real-time allows for the detection of indirect indicators of compromise, such as the abnormal system resource consumption noted during SSH logins.
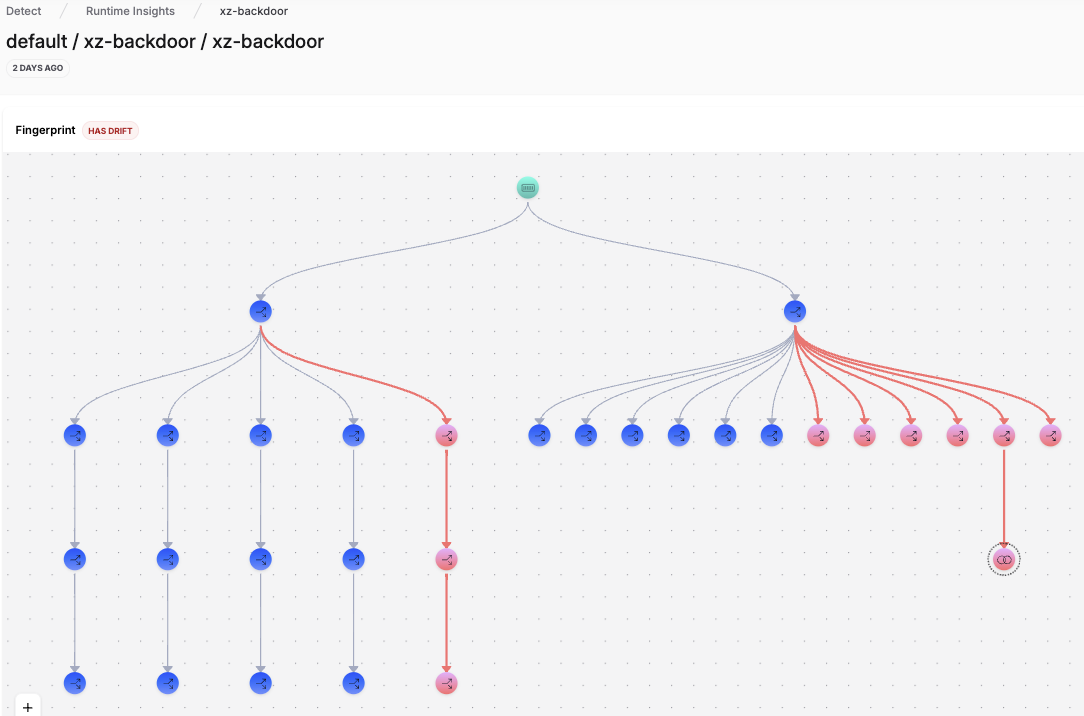
If you had been using RAD fingerprints for sshd prior to the attack, you would have seen the drift. It would have looked like the example fingerprint below, in the case of the XZ Backdoor.
Through comprehensive behavioral analysis, the RAD Security drift detection engine can not only alert on these discrepancies but also help in unraveling the complex web of execution paths that a sophisticated backdoor might employ.
Drift Detection from XZ Backdoor Exploit
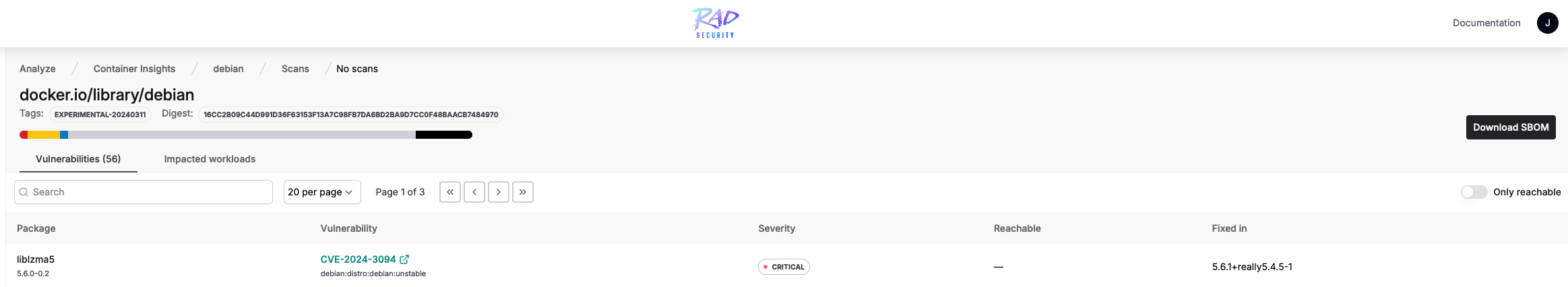
You can also use RAD's packages inventory page to find where XZ Utils is installed. Here you'll see which packages have been scanned that have CVEs, the version they're running, and the affected workload, and you can do a quick search.
XZ Utils in package inventory page
Conclusion
The XZ Utils backdoor incident illustrates the evolving complexity of supply chain attacks and the imperative need for advanced detection mechanisms. Behavioral eBPF runtime security remains a critical tool and necessary in the cybersecurity arsenal, offering the granular visibility and proactive threat detection necessary to counter these insidious threats effectively. As the cyber landscape continues to evolve, so must our approaches to securing it, with a keen focus on the behaviors that define normal and malicious activities alike.


.png?width=300&name=Group%2010694%20(1).png)
