In network security, micro-segmentation has emerged as a cornerstone for implementing Zero Trust security models across cloud and cloud native environments alike. In the case of cloud native and Kubernetes environments, micro-segmentation follows the re-architecture of many applications from monolithic models into microservices via containers, where smaller services are performed separately, with service segmentation at a granular level.
By controlling access to each segment, micro-segmentation minimizes the risk of unauthorized access, making it a key component in modern security architectures. In this article, we will explore the critical role of micro-segmentation in securing Zero Trust architectures. We will further demonstrate how security teams can use micro-segmentation to enforce the principle of least privilege across specific applications, servers, and complex network traffic flows.
Demo KSOC to enforce least privilege access in your Kubernetes environment
How Does Micro-Segmentation Work?
From a classic cloud security perspective, micro-segmentation refers to any approach that creates network segments. These segments can then take on different security policies. For example, every cloud environment will allow for Virtual Private Clouds (VPCs) that are a logically isolated virtual network, with internal subnets for internal traffic and a gateway for traffic external to the VPC. This is micro-segmentation in the context of the cloud.
In the context of Kubernetes, micro-segmentation takes the form of network security groups and policies which will direct traffic as you dictate, for example:
- from the load balancer to pods
- Between back-end applications and frontend services
- From applications to the appropriate database components
This is all in the broader context of Kubernetes network security, which includes load balancing, ingress and egress, and Endpoint Slices. The default networking capabilities will be different from cloud to cloud, depending on whether you have deployed Kubernetes via EKS, AKS, GKS, or another provider.
Micro-segmentation is a constant area of improvement and change in Kubernetes. For example, in the Kubernetes version 1.29 release, there is a new alpha capability to solve the current limitation where clusters sometimes run out of available IPs. With the new capability, users would be able to increase the availability of IPs assigned to Services. Staying updated to the latest Kubernetes version ensures all the micro-segmentation solutions available are also accessible.
Why is Zero Trust so important to your security strategy?
Zero Trust is the concept of never trust, always verify, that can be applied in any number of ways across an IT environment. Traffic coming internally from one pod to another? Don’t trust it - figure out a way to verify it even if both resources are internal. Valid credentials being used to access your S3 buckets in the cloud? Verify that this usage of credentials is legitimate with MFA or other additional identity controls.
Zero Trust has become an even more critical concept for security leaders, based on the growing reliance of attackers on identity to carry out attacks.
In a recent report from Crowdstrike, it was found that attackers were shifting toward the malicious usage of valid credentials versus malware to gain access as well as persistence in an environment. In terms of evasion tactics, attackers were also less inclined to go the classic route of disabling firewalls and log-tampering, in favor of finding ways to modify how legitimate credentials were created, and how to impersonate or steal identities.
In the IBM Cost of the Data Breach study in 2023, stolen and compromised credentials represent the second most common initial attack vector, malicious insiders constituted the most costly initial attack vector, and breaches initiated with stolen or compromised creds and malicious insiders took the longest to resolve when compared to other initial attack vectors like phishing or zero day vulnerabilities.
Zero trust has become a key part of CISO’s initiatives in 2024, but to really reduce the attack surface, it must reach beyond unauthorized access and credentials to include micro-segmentation.
Why Micro-Segmentation Supports a Zero Trust Security Posture
From a security perspective, micro-segmentation reduces the blast radius of a breach and can be a key clue in the incident response process.
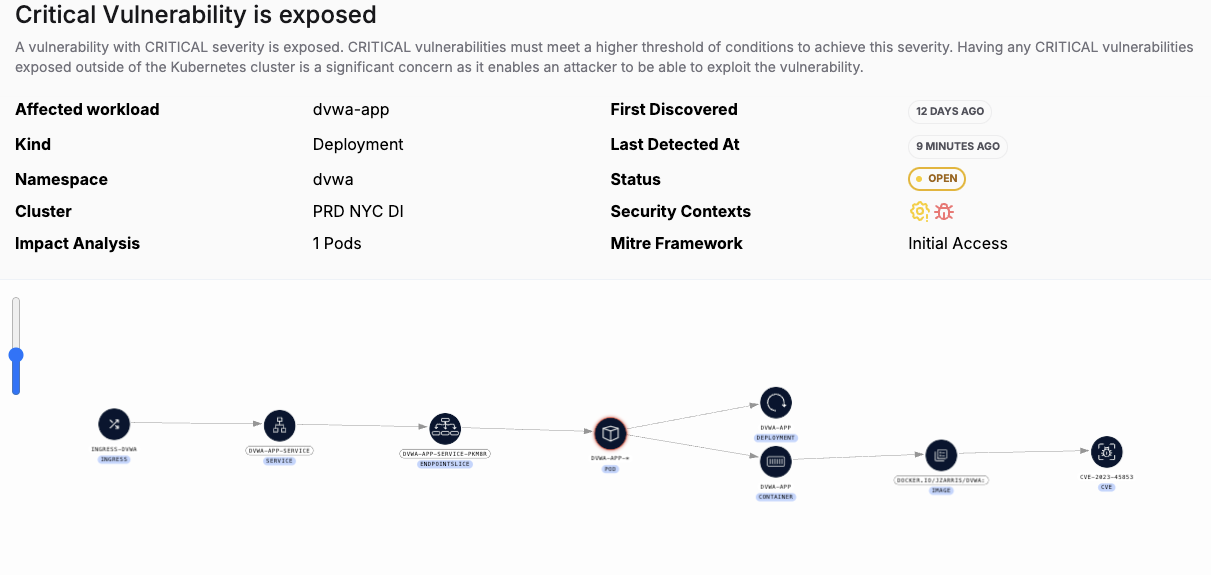
A network issue can either increase or decrease the blast radius of an attack. For example, take this threat vector, which shows that a running image with a critical vulnerability is also, through the network and various micro-segmentation policies, is also exposed to the internet through the ingress and the Application Load Balancer (ALB) in the EKS instance where this cluster is deployed. This network exposure represents a violation of zero trust principles, as they apply to microsegmentation, and the open exposure to the internet must be addressed. On its own, the critical CVE might not be an issue. But combined with the micro-segmentation issue, the blast radius has now been increased and the CVE is now a top priority issue.
Here is another threat vector with a micro-segmentation issue, in that an over permissioned identity (in this case, a machine identity, or serviceaccount) is tied to a workload that is exposed to the internet. So there are two zero trust violations: the over permissioned identity (which should instead have only least privilege access) and the unnecessary internet exposure of the workload itself. On its own, the over permissioned identity is not perhaps a critical priority. But combined with the exposure issue, the potential blast radius has now been increased.
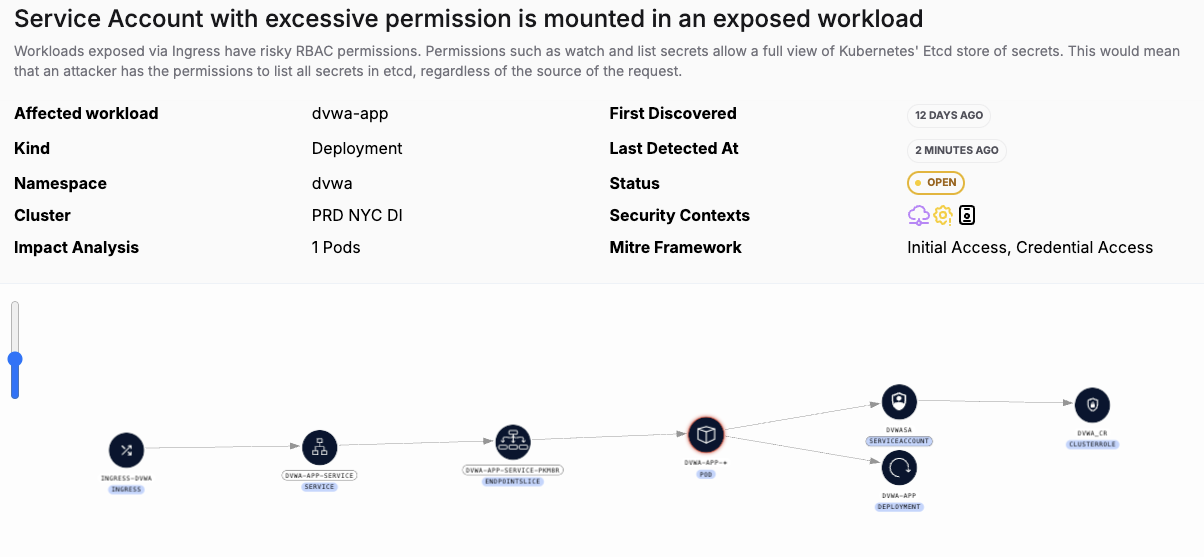
In both of these examples, the blast radius of a potential attacker taking advantage of a critical CVE or an overly permissioned identity is amplified because of the micro-segmentation issue - which also happens to violate Zero Trust principles.
Another example of a well-known failure of micro-segmentation in a zero trust architecture can be found with the Instance Metadata issue in EKS, known as IMDSv1. The IMDSv1 endpoint provides credentials for node roles. Until you set policies governing the node role, there are default permissions that apply and can be used to map out the entire cloud network, including network security groups, IP addresses, VPCs, and any associated subnets or route tables. The default Container Networking Interface, or CNI, policies could also be used to modify the IP address of the worker node, which could be tampered with in many ways to cause DoS attacks or other subversive goals. In 2023, there was a Kubernetes attack from Scarleteel that leveraged the weakness of IMDSv1 to accomplish broad lateral movement and data exfiltration.
The importance of applying zero trust security principles to micro-segmentation in a Kubernetes environment cannot be understated, as an important way to prevent attacks. From the perspective of incident response, getting a view into network behavior via audit logs is a key indicator of compromise.
How Do Security Teams Implement Micro-Segmentation?
Security teams have little time, too many attack vectors and must find a way to become more efficient. KSOC helps security teams figure out where micro-segmentation issues lie in the list of other issues that need attention and might be impacting your ability to implement a zero trust strategy in Kubernetes and the cloud. KSOC uses threat vectors to combine network issues with other risks in your Kubernetes environment, like critical CVEs or RBAC over permissions.
Threat vectors map all the Kubernetes components together in real-time across the cloud, network, runtime, images, Kubernetes misconfigurations, RBAC and Cloud identity, to identify those areas where micro-segmentation is part of a larger group of issues. As in the example above, you may have a critical CVE, but on its own it is possibly not so important, or not even running in your environment. But if it is exposed in a running container to the internet through the ingress and also through the cloud, you have a top priority issue that an attacker could exploit.

After you know where micro-segmentation sits in your list of overall priorities for implementing a zero trust strategy, the second thing you need to do is enforce the principle of least privilege, both from an identity perspective as well as from a networking perspective. On the part of identity, this can be done with admission control and right-sizing Kubernetes role based access control policies. On the side of networking, you will need to set up your network groups and policies and be very aware of the default policies that have to be modified if you deploy Kubernetes in the cloud.
What is the Future of Micro-Segmentation and Zero Trust?
As multi-tenancy in Kubernetes continues to become a necessity for businesses, and deploying Kubernetes via the cloud continues to gain in popularity, micro-segmentation will become a more and more critical part of a broader zero trust strategy. But it is not alone; there are many other parts to a zero trust strategy that must be taken into consideration. Teams are busy and cannot afford to just look at one area of Kubernetes - they need to be able to see the whole thing, as a moving, dynamic environment, to pick out the top priorities to address. Kubernetes can be a very effective control for the blast radius of any attack, but if configured improperly, the opposite is true.
Get in touch with the team today to see how to understand the top risks to your zero trust architecture using KSOC threat vectors today.