Today we are announcing the evolution of Kubernetes Security Operations Center (KSOC) to RAD Security! While KSOC will remain a critical part of the RAD Security umbrella, we are renaming to RAD Security to signify our commitment to a new era of behavioral cloud native detection and response that can combat today’s evolving threats.
Let's make security truly RAD!
Why RAD?
RAD stands for itself; it represents security that truly delivers. Our commitment to our customers is that simple; we strive to provide security that doesn't just meet expectations—it exceeds them, forming a useful part of security teams’ everyday motions, so they can focus on innovation. This was consistent with the mission of KSOC, but now our name will speak this commitment even more clearly and loudly.
RAD Security is not:
- An acronym that stands for something more complicated.
- A complicated, deep allusion to cultural commentary.
- An analogy for something else.
- Complicated.
- It’s just RAD.

Why are we renaming KSOC to RAD Security?
The industry needs to head toward positive security models that are declarative, verifiable and portable. We pioneered the RAD security cloud native workload fingerprint standard, and launched a free online catalog for open source images with the goal of demonstrating that it is possible to categorize the acceptable behavior of a workload without duplications, and at a meaningful level for detecting drift and attacks.
KSOC stood for Kubernetes Security Operations Center; as the portfolio of products increases, the name change will remove any confusion as to the overall scope and evolution of the offering.
As KSOC, multiple industry-first milestones were hit, and now form part of the holistic RAD Security behavioral cloud native detection and response platform:
- First real-time KSPM solution
- First Kubernetes Bill of Materials (KBOM)
- First cloud native Identity Threat Detection and Response (ITDR) solution
- First standard for cloud native workload fingerprints
KSOC is a critical part of the RAD platform moving forward, as a real-time KSPM product alongside cloud native identity Threat Detection and Response (ITDR) and Zero Day detection and response in the software supply chain and runtime.
Momentum in the Market
The name change to RAD Security reflects evolution as a result of considerable momentum in the market. In the last year alone, ARR has grown by 3 times, with a 100% retention rate of our customers from the last two years. Net new logos from highly regulated and digitally mature industries such as insurance, banking and media reflect the importance of cloud native technologies in the security team’s purview and priorities, as well a commitment on our side to security, for example with our SOC2 certification.
A growth of 60% in customer contract value, as well as almost half of new ARR coming from land and expand motions, speaks volumes to the growing need as well as our ability to penetrate new markets while affirming the trust and satisfaction of current customers in our solution.
Real-time KSPM is a critical part of detection and response
Real-time KSPM is a critical part of a detection and response solution, because much of the ‘response’ in cloud native environments is accomplished in the long-term via shift-left, and because it can provide critical context for the detection itself.
KSOC’s real-time posture shows the posture of what is actually running (including scanning and SBOMs), and provides unmatched prioritization, by combining the risk of multiple components across Kubernetes in the form of real-time threat vectors, and other features such as CVE Exploitability. This, combined with information about where your actual incidents might be taking place, gives a holistic view of prioritized risk and urgent issues in a way that no point solution for runtime or KSPM could provide.
Real-time posture is a requirement for cloud native detection and response, and KSOC is the only real-time Kubernetes Posture Management (KSPM) tool on the market, allowing you to verify the posture of your cloud native infrastructure to the second.
Features include:
Threat vectors
- Prioritize your top risk in real-time across runtime, the network, image CVEs, K8s misconfigurations, the cloud and identity
- Real-time, to-the-second, view of Kubernetes misconfigurations, tied to the Kubernetes lifecycle
- 5 Minute installation and configuration
- Risk Explorer visualizes and filters a live-stream view of the environment
Threat vector screenshot
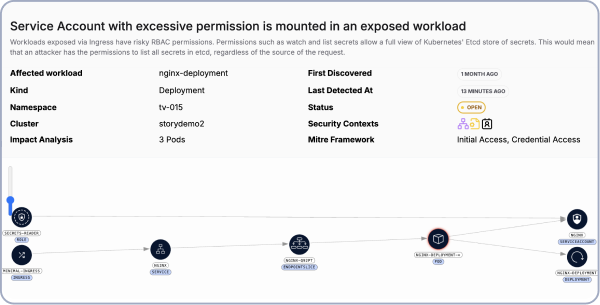
Guardrails & Admission Control:
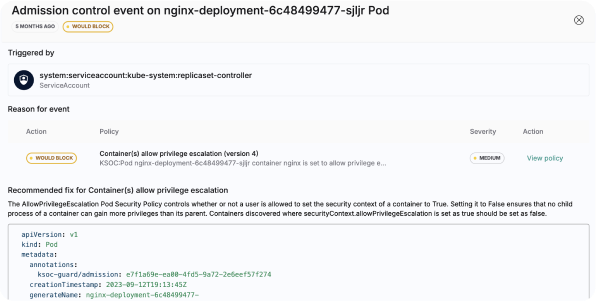
- Prioritize CVEs based on exploitability in runtime
- Admission control that is OPA compatible
- In-cluster policy enforcement and optional 'dry run' mode
- GitHub Actions CI Worklflow to remediate policy or scan for CVEs earlier in the lifec
- Identify vulnerabilities in running images
- Manage workload policy centrally in the CI
Admission Control Example
Compliance and Reporting:
- Generate SBOMs for running containers
- Generate KBOMs for cluster configuration
- Benchmark against NSA and CIS guidelines
- Generate reports across multiple clusters
Cloud native detection & response is broken
According to RedHat’s State of Kubernetes Security report in 2023, 90% of respondents reported incidents in their container or Kubernetes environments. Today’s cloud native detection and response solutions are ineffective against Advanced Persistent Threats and sophisticated attackers:
A new report from the FiveEyes says that the same threat actors responsible for the SolarWinds breach are utilizing new Tactics, Techniques and Procedures (TTPs), aimed at:
- Cloud infrastructure
- Service accounts, and unused identities
The most common attack type in 2023, according to IBM’s cost of the data breach report, were software supply chain attacks .
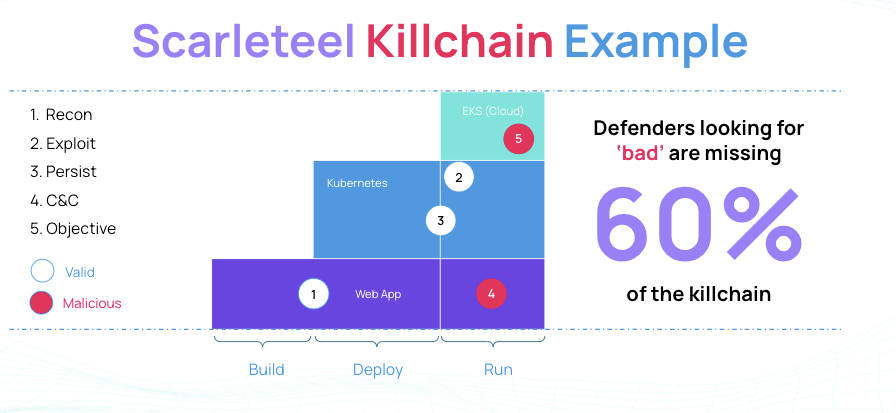
Picking apart the Scarleteel attack from 2023 that targeted cloud native infrastructure, it’s clear that defenders focused on malicious activity would have only spotted 60% of the attacker’s kill chain. The killchain is a classic one for cloud native environments:
- The attacker starts by exploiting a vulnerability in a web app hosted in Kubernetes
- Proceeds to launch a campaign to steal cloud credentials
- Uses those cloud credentials to exploit Kubernetes further
- Creates its own set of valid identities and credentials
- Installs a botnet and accomplishes its task of stealing data from the cloud
In the case of this attack and other sophisticated attacks, as you can see, if you were to only look for malicious behaviors in this killchain, you would clearly miss an entire 60% of the attack which relied on valid permissions, identities and programs. And once again, we see that the attacker relied on a mix of cloud native infra, identity, and the software supply chain to accomplish its attack.
To improve the defender’s position, cloud native detection and response solutions must include:
- Cloud native Identity Threat Detection and Response (ITDR)
- Real-time (Real-time KSPM)
- A behavioral, positive security model that includes valid behaviors and programs in detection and response
What is missing from today’s solutions?
Today, even though defenders can verify they have security measures, they have no real way to detect the sophisticated attacks through the new TTPs of the most prolific threat actors. This is because:
- Most detection solutions take a one-size-fits-all approach to detection, relying on stateless signatures, versus telling you what your unique environment should look like matched to actual behavior
- ITDR solutions are completely missing Kubernetes RBAC insight, or if they include it, leave out how the identities are actually being used and instead focus on over permissions
- Software supply chain security has been relegated to Software Composition Analysis (SCA), Software Bills of Materials (SBOMs), and scanning for vulnerabilities
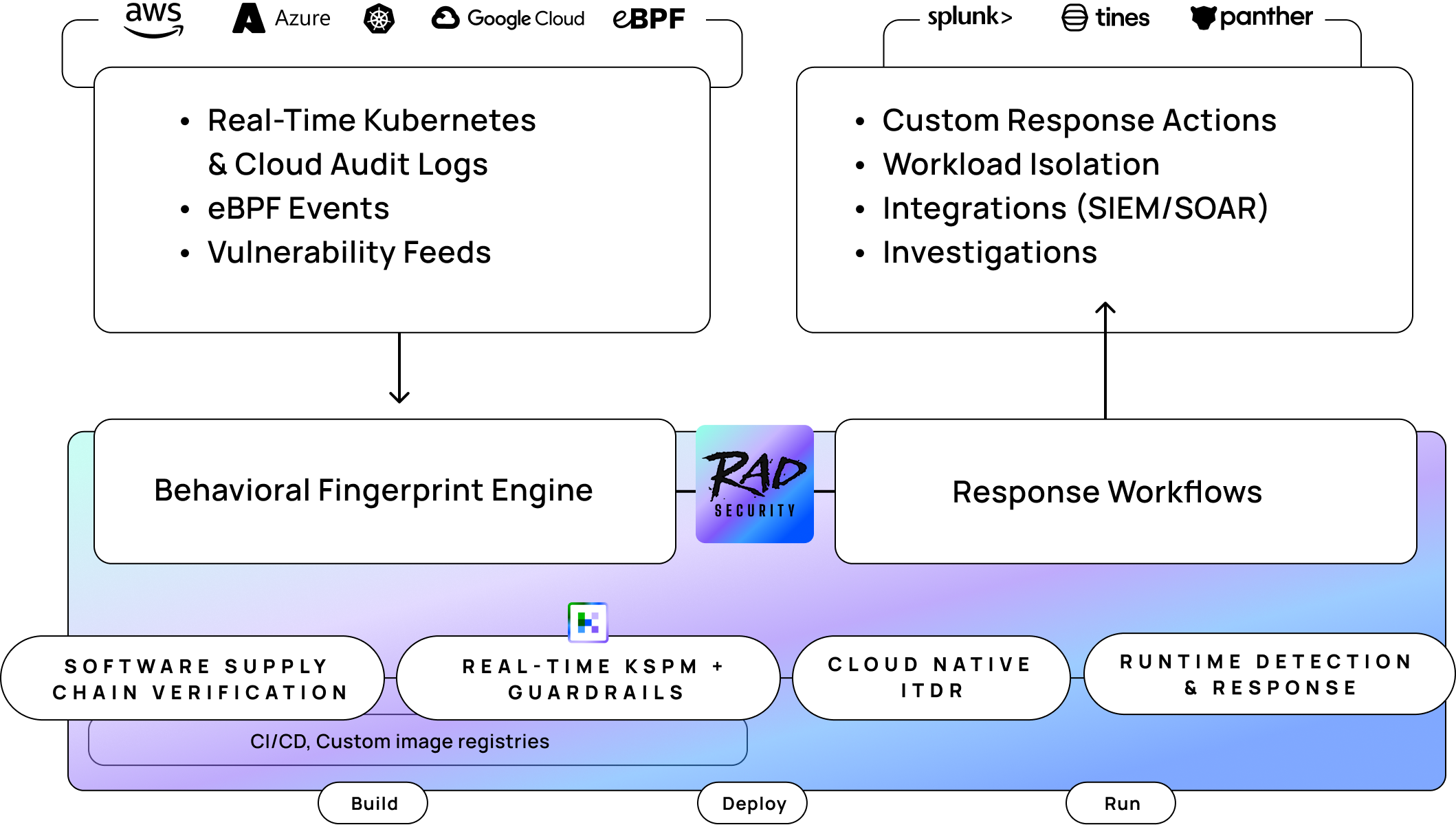
What is RAD’s Behavioral Cloud Native Detection and Response platform?
The answer to catching sophisticated attacks is a behavioral approach to cloud native detection and response that covers cloud native infra, identity and the software supply chain.
The RAD platform creates behavioral fingerprints of your unique good behavior across the software supply chain, cloud native infra, workloads and identities, to detect zero day attacks and sharpen inputs into shift-left and posture management.
Read more about cloud native workload fingerprints, visit the RAD Security product page, or visit the free online fingerprint catalog to learn more.
Conclusion
RAD Security is a simple name, reflecting a big goal: Eliminate zero day attacks in your cloud native environment. This can only be done with a RADical new approach, and changing our name to RAD Security reflects that vision.
Reach out to the team to sign up for any of our early access programs, to detect drift based on unique fingerprints of cloud native workload behavior in your environment.
Sign up for Early Access Programs



