Intro
KSOC recently launched Automated Risk Triage, powered by threat vectors, to improve the efficiency of cloud native security for those using Kubernetes. These capabilities show risk through a combined view of Kubernetes’ component parts, in real time and tied to the Kubernetes lifecycle. In doing so, threat vectors can reduce the time to triage Kubernetes risk to your next coffee break while providing a never-before-seen view of your Kubernetes risk. In this blog we will go into detail on what a threat vector is, how it compares to other solutions, and how to get started.
What is a threat vector?
As mentioned in our discussion of what it means to take a Kubernetes-first perspective of cloud-native security, threat vectors highlight critical risk based on the combined risk of connected Kubernetes components.
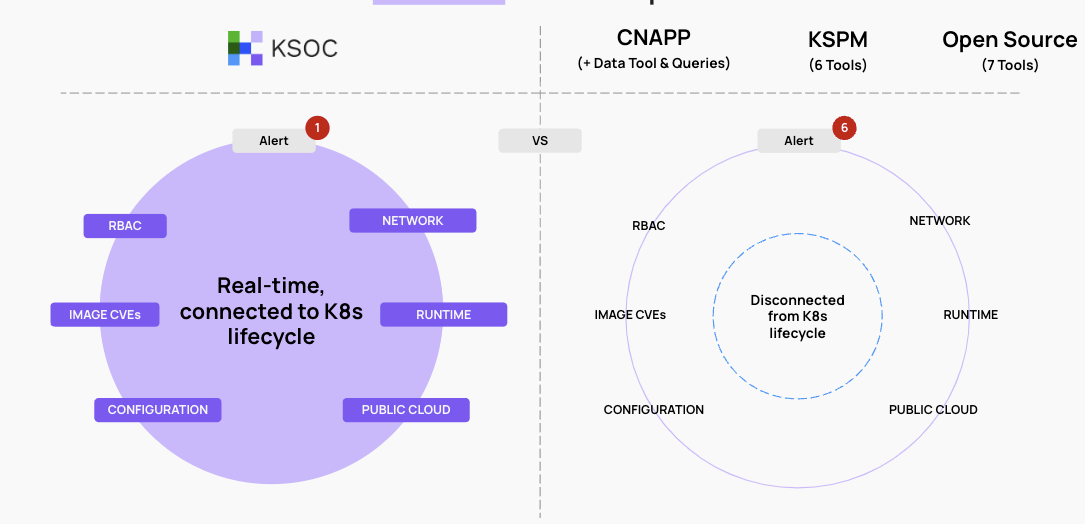
In the example below, a threat vector combines the risk of various Kubernetes components across configuration of the Kubernetes manifest, RBAC policies, image CVEs, network and public cloud exposure as well as runtime alerts. Through this combination of risky factors, you can immediately understand your top, most critical risk. Importantly, as must be true with a Kubernetes-first approach, these factors are all tied to the Kubernetes lifecycle and represent real-time, accurate risk.
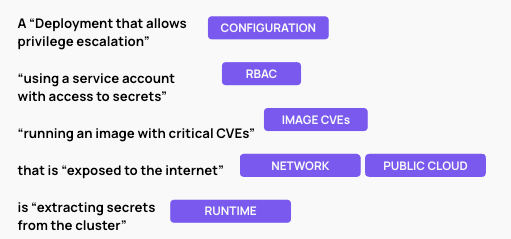
Cutting days of work
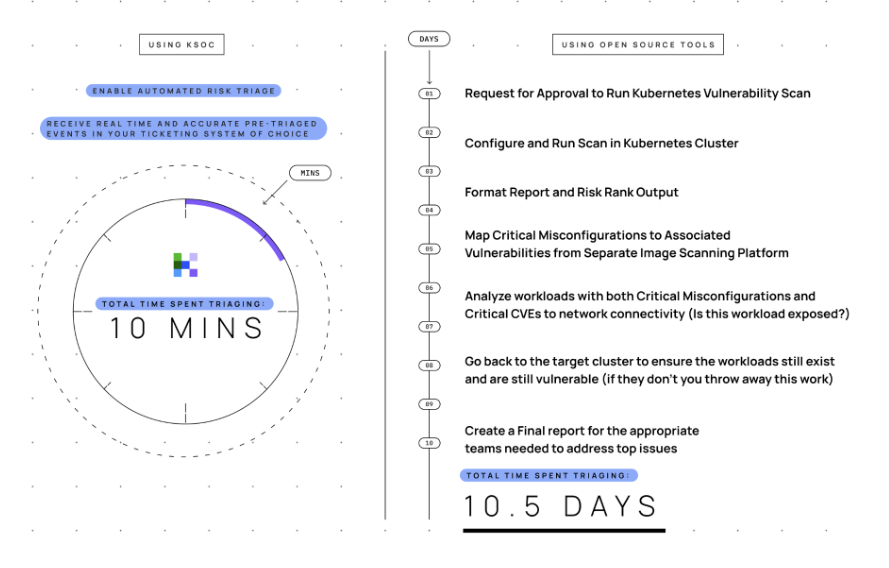
Threat vectors save practitioners massive amounts of time. Before KSOC, a security engineer would typically take days to create a report of the top issues across their clusters. And once arriving at this point, it’s not clear whether the same issues would still be relevant because the cluster might have changed while they were compiling the report. It’s likely they might have to start the work all over again. With KSOC threat vectors, you would never have to do any re-work and the critical, prioritized risk is available.
In the example below, we show how you might go about getting the equivalent of threat vectors using open source solutions. The difference shows up in days of work.
If we were to try the same thing with commercial KSPM solutions or Cloud Native Application Protection Platforms (CNAPP) we would run into the same issues.
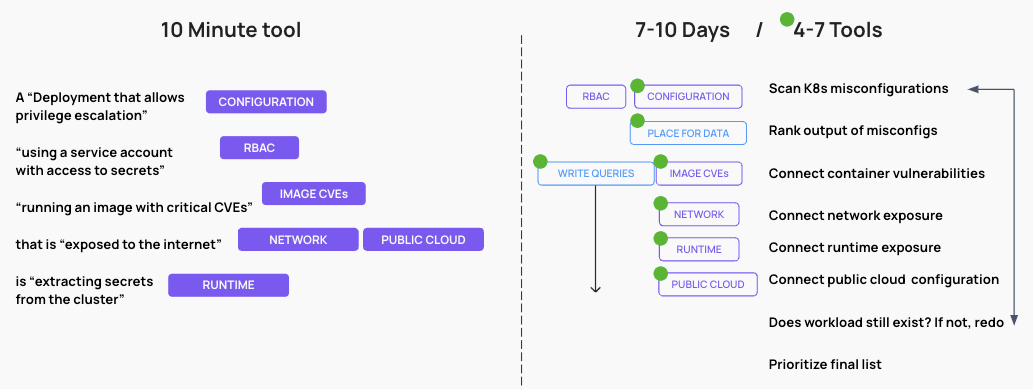
Critically, none of these alternatives would show the Kubernetes data in real-time. So it is possible to get to the last stage of the process and find that the workload doesn’t exist anymore. This could double or triple the time it takes to get what, with KSOC, takes 10 minutes.
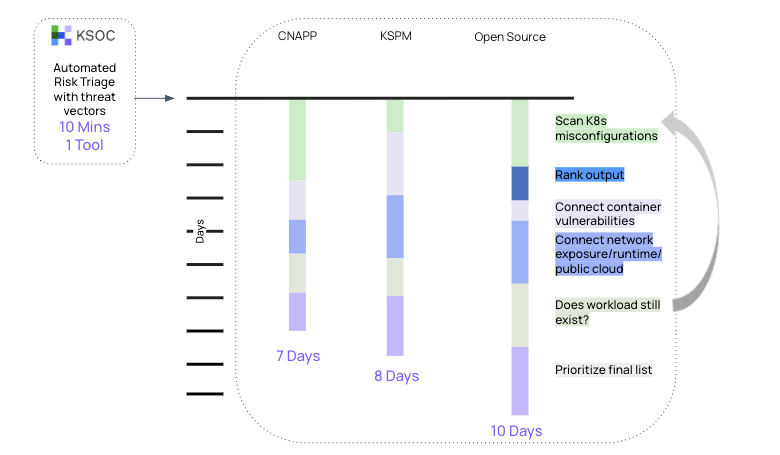
With any other solution on the market, you are looking at a 7-10 day project and 4-7 tools, even if you are using a CNAPP, because you will need somewhere to put the added data and somebody to write the queries to connect the data. If you are using only open source, you might need 7 tools or more.
With threat vectors, we reduce 6 alerts into one alert that represents critical risk.
With this approach, you will also be reducing the amount of time engineering spends re-working code, because less risks will make their way to engineering’s desk as security has a better way to triage real risk.
The manual processing of individual security findings to find your actual risk will be reduced dramatically, as you get a full, historical view of what is happening across your Kubernetes components in real-time.
Getting started with threat vectors
Here is how easy it is to start reducing noise and saving time:
Step 1. (5 minutes) Connect to KSOC, which will create a real-time graph model of your clusters
Step 2. (5 minutes) Threat Vectors collect and correlate real time event streams to deliver a highly actionable and precise view of risk across multiple Kubernetes components, including the Kubernetes manifest, container vulnerabilities, RBAC, runtime, the public cloud and more. Receive real time and accurate pre-triaged events in your ticketing system of choice.
.png?width=2236&height=1452&name=image%20(8).png)
Step 3. (15 minutes) Query and analyze all of your cluster security data - runtime, misconfigurations, image security and RBAC - and how it contributes to your overall risk
.png?width=2712&height=1618&name=image%20(6).png)
.png?width=2290&height=1438&name=image%20(7).png)
Step 4. (5 minutes) Build and share a compelling case for the engineering team for ‘why should this be fixed’, reducing your homework on your overall issues to minutes
-1.png?width=1432&height=800&name=image%20(5)-1.png)
Step 5. (any amount of time) Spend time doing all the things you weren’t able to get to before using KSOC
Conclusion
Threat vectors do the hard work of combining risk across various components of Kubernetes in real-time so you always know what your top risk looks like. This is a core requirement for a Kubernetes-first view of cloud native security, and it is the core component underlying Automated Risk Triage. It is important to note that you would not be able to get this kind of a perspective on your Kubernetes environment with anything other than a real-time connection to the Kubernetes lifecycle. And though Kubernetes is often used as a cloud service, if you are using Kubernetes, cloud security is inefficient (even with Kubernetes-specific features tacked on) because it will not tie Kubernetes components together in real-time. To learn more and see threat vectors live in your environment today, contact us for a demo!



